Top 25 Kali Linux Penetration Testing Tools

Kali Linux is often thought of in many instances. It is, however, one of the most current and popular flavors of Linux containing the most popular tools available to security professionals.
Kali Linux is an open-source distribution based on Debian focused on providing penetration testing and security auditing tools. Actively developed by Offensive Security, is not only a pentester, or Red Teamer, researcher, analyst, or examiner’s dream, but a rather nice flavor of Linux that boasts an operating system filled with a pentesting tools, containing a robust package of programs that can be used for conducting a host of security-based operations. One of the many parts in its division of tools is the forensics tab. This tab holds a collection of tools that are made with the explicit purpose of performing digital forensics.
Forensics is becoming increasingly important in today’s digital age where many cyber crimes are committed using digital technology, having an understanding of the forensics can greatly increase the change of making certain that criminals don’t get away with a crime.
One of the best things about Kali is the fact that it doesn’t require you to install the OS in your hard drive — it uses a live image that can be loaded in your RAM memory to test your security skills with the more than 600 ethical hacking tools it provides.
It includes numerous security-hacker tools for information gathering, vulnerability analysis, wireless attacks, web applications, exploitation tools, stress testing, forensic tools, sniffing and spoofing, password cracking, reverse engineering, hardware hacking, and much more.
Kali Linux uses what are called “Kali Linux Metapackages” — these metapackages allow you to install sets of tools, instead of requiring you to install all the available Kali Linux tools in the repo.
For example, if you’re only going to use Kali Linux tools for wireless security assessments, then you can simply generate a Kali ISO image and include the kali-linux-wireless metapackage only.
This article is aimed at giving you an overview of the best Kali Linux Tools in general, regardless of the metapackages to which they belong.
I’m going to start with the programs as they appear in the forensics menu:
🔹Autopsy🔹
A tool used by the military, law enforcement, and other entities when it comes to performing forensic operations and investigations. This package is probably one of the most robust ones available as open-source. It combines the functionalities of many other smaller packages that are more focused in their approach into one neat application with a web browser-based UI.
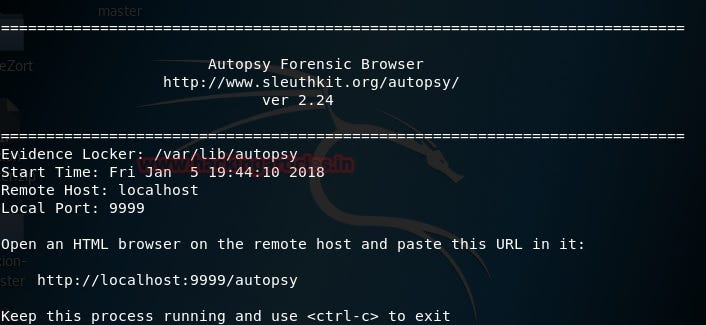
It is used to investigate disk images. When you click on Autopsy, it starts the service and its user interphase can be accessed on the web browser at: https://9999:Localhost/autopsy. It gives the user a full range of options required to create a new case file: Case Name, Description, Investigators Name, Hostname, Host time zone, etc.
Its functionalities include — Timeline analysis, keyword search, web artifacts, hash filtering, data carving, multimedia, and indicators of compromise (IOC). It accepts disk images in RAW or E01 formats and generates reports in HTML, XLS and body file depending on what is required for a particular use.
Its robustness is what makes it such a great tool, be it case management, analysis, or reporting, this tool has you covered.

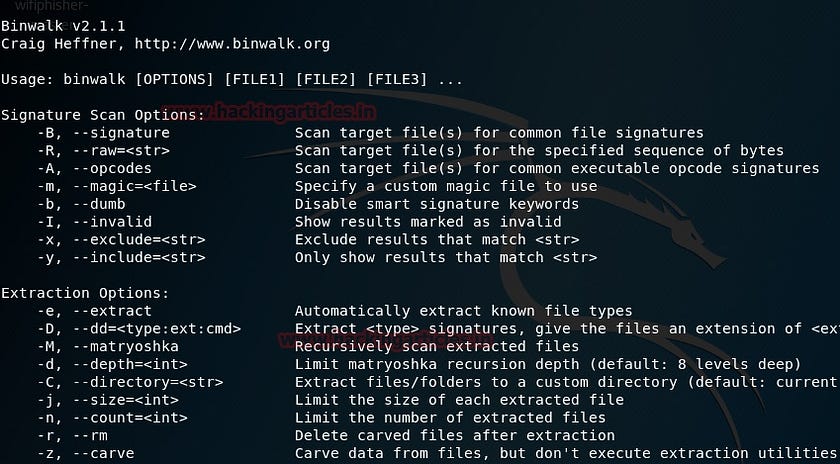
🔹Binwalk🔹
This tool is used while dealing with binary images. It has the capability of finding the embedded file and executable code by exploring the image file. It is a very powerful tool for those who know what they are doing. If used right, it can be find sensitive information hidden in firmware images that can lead to uncovering a weakness or vulnerability, or even a loophole to exploit.
This tool is written in Python and used the libmagic library, making it perfect for usage with magic signatures created for a Unix file utility. To make things easier for investigators, it contains a magic signature file which holds the most commonly found signatures in firmware, making it easier to spot anomalies.
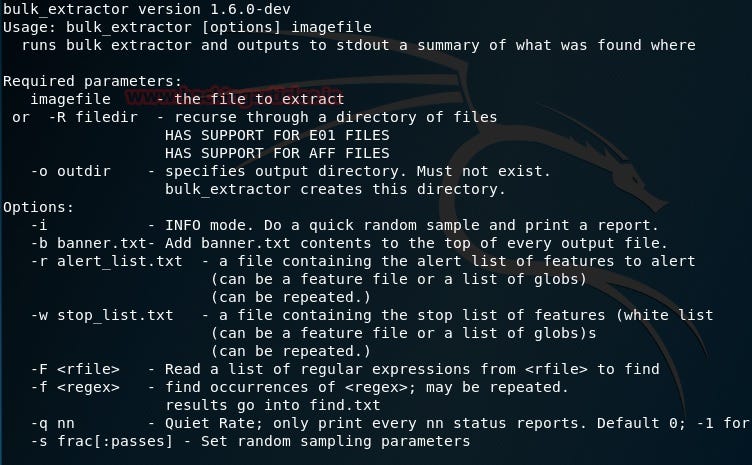
This is a very interesting tool when an investigator is looking to extract certain kinds of data from the digital evidence file. This tool can carve out email addresses, URLs, payment card numbers, PII, etc. This tool works on directories, files, and disk images and if data is partially, or completely corrupted — it can be compressed and this tool will find its way into it.
The tool comes with features which help to create a pattern in the data that is found repeatedly, such as URLs, email IDs, and more. It presents them in a histogram format, and has a feature by which it creates a wordlist from the data found. This is huge as it can greatly assist investigators in cracking the passwords of encrypted files.
This program is most used in a live boot setting. It is used to locally check the host for any installed rootkits. It comes in handy when trying to harden an endpoint or making sure that a hacker has not compromised a system.
It has the capability to detect system binaries for rootkit modification, last log deletions, quick and dirty string replacements, and temp deletions. This is just a taste of what it can do. The package seems simple at first glance, but to a forensic investigator, its capabilities are invaluable.

🔹Foremost🔹
First and foremost, this application can aid in fetching deleted files which may have been deleted by accident and that might help to solve a digital incident. Foremost is an easy to use open-source package that can carve data out of formatted disks. The filename itself might not be recoverable, but the data it holds can be carved out.
Foremost was written by U.S. Air Force special agents. It can carve files by referencing a list of headers and footers even if the directory information is lost. This makes for fast and reliable recovery.

🔹Galleta🔹
When following a trail of cookies, this tool will parse them into a format that can be exported into a spreadsheet program.
Understanding cookies can be a tough nut to crack, especially if the cookies might be evidence in a cyber-crime that was committed. This program can lend a hand by giving investigators the capability to structure the data in a better form and letting them run it through an analysis software, most of which usually require the data to be in some form of a spreadsheet.

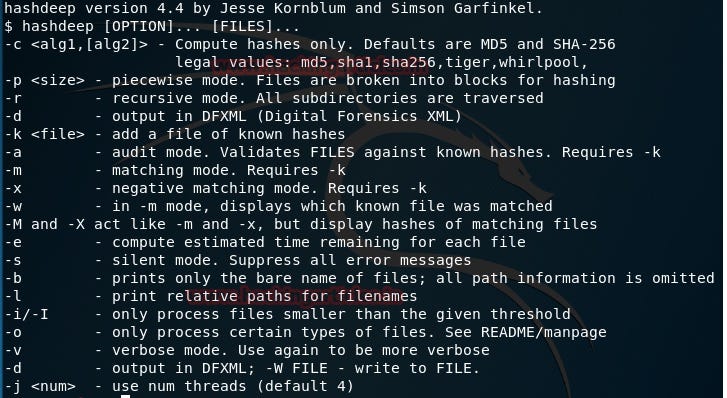
🔹Hashdeep🔹
This program is a must when dealing with hashes. Its defaults are focused on MD5 and SHA-256. It can be existing files that have moved in a set or new files placed in a set, missing files, or matched files. Hashdeep can work with all of these conditions and give reports that can be scrutinized.
One if Hashdeep’s biggest strengths is performing recursive hash computations with multiple algorithms, which is integral when the time is if the essence.
🔹Volafox🔹
Volafox is a memory analysis tool that is written in Python and focuses on memory forensics for macOS and OSX. It works on i386 and IA-32e frameworks, If you’re trying to hunt malware or any other malicious program that was, or is residing in system memory, this is the way to go.
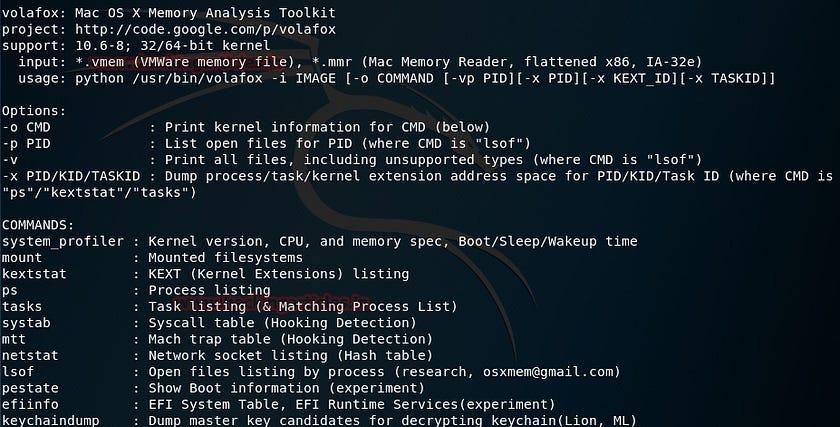
Probably one of the most popular frameworks when it comes to memory forensics. This is a Python-based tool that lets investigators extract digital data from volatile memory (RAM) samples. It is compatible to be used with the majority of the 64bit and 32bit variants of Windows. Selective flavors of Linux distros including Android. It accepts memory dumps in various forms, be it raw format, crash dumps, hibernation files, or VM snapshots. It can give a keen insight into the run-time state of the machine. This can be done independently of the host’s investigation
Here’s something to consider: decrypted files and passwords are stored in the RAM, and if they are available, investigating files that might be encrypted in the hard disk can be a lot easier to get into and the overall time of the investigation can be considerably reduced.
🔹t50🔹
t50 is a web-stress testing tool included with Kali Linux. It can help you test how your websites, servers, and network react under high load average during an attack.
It’s one of the few security tools capable of encapsulating protocols using GRE (Generic Routing Encapsulation), and supports up to 14 different protocols. The t50 package also lets you send all protocols sequentially using one single SOCKET. t50 features:
- DoS and DDoS attack simulator
- Main supported protocols include TCP, UDP, ICMP, IGMP, etc.
- Up to 1,000,000 pps of SYN Flood if using Gigabit network
- Up to 120k pps of SYN Flood if using 100Mbps network

Inundator is a multi-threaded IDS evasion security tool designed to be anonymous. By using Tor, it can flood intrusion detection systems (especially with Snort) causing false positives, which hide the real attack taking place behind the scenes. By using the SOCKS proxy, it can generate more than 1K false positives per minute during an attack.
The main goal of Inundator is to keep your security team busy dealing with real attacks when they’re happening, and not tied up dealing with false positives. Inundator features:
- Multi-threaded capabilities
- Full SOCKS support
- Anonymization-ready
- Support of multiple targets
- Queue-based
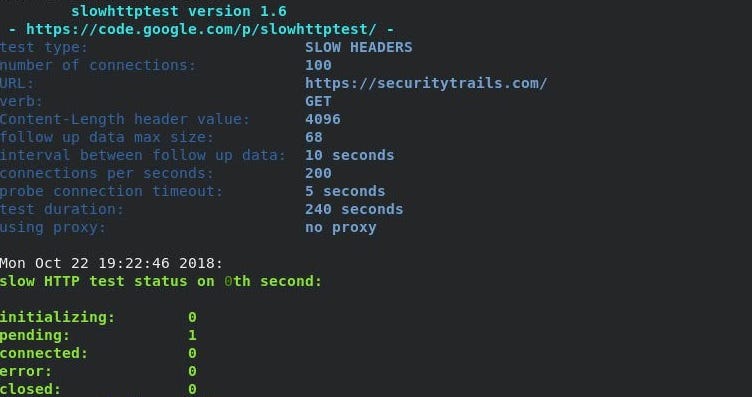
SlowHTTPTest is one of the most popular web-stress applications used to launch DoS attacks against any HTTP server. This type of security tool focuses on sending low-bandwidth attacks to test your web-server health and response times. It includes statistics of all your tests and allows you to run multiple types of attacks such as:
- Apache Range Header
- Slow Read
- Slow HTTP POST
- Slowloris
Main features include:
- Saving statistics output in HTML and CSV files
- Setting verbose level (0–4)
- Targeting custom number of connections
- Setting HTTP connection rate (per seconds)
- Proxy traffic redirection
🔹FunkLoad🔹
Written in Python, FunkLoad is a popular web-stress tool that works by emulating a fully functional web browser. It’s highly useful for testing web projects and seeing how well they react in terms of web server performance.
FunkLoad allows full performance testing to help you identify possible bottlenecks within your web apps and web servers, at the same time testing your application recoverability time.
Main FunkLoad features include:
- Real web browser emulation (including GET/POST/PUT/DELETE, DAV, cookie, referer support, etc.).
- Command-line advanced tests
- Full benchmarking reports in PDF, HTML, ReST, Org-mode
- Test customization using a configuration file
- Full support for popular servers such as PHP, Python, Java.
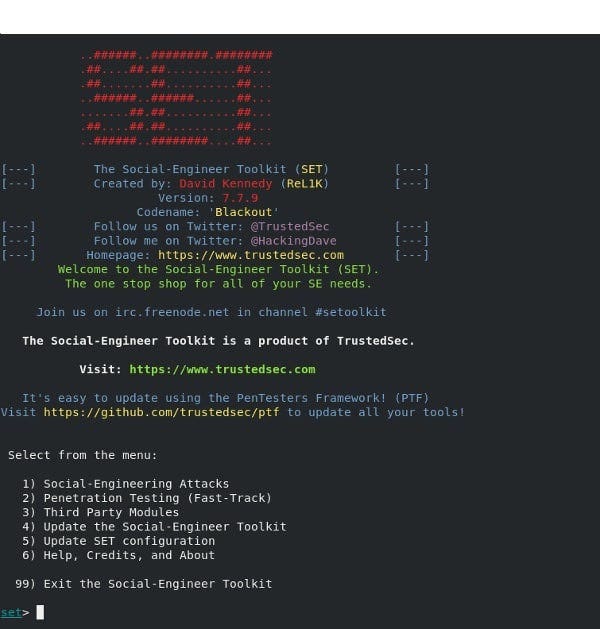
🔹Social Engineering Toolkit (SET)🔹
Available for Linux and Mac OS X, the Social Engineering Toolkit (known as SET) is an open-source Python-based penetration testing framework that will help you launch Social Engineering attacks in no time.
Have you ever wondered how to hack social network accounts? Well, SET has the answer — it’s indispensable for those interested in the field of social engineering.
What kind of attacks can I launch with SET?
- WiFi AP-based attacks: this kind of attack will redirect or intercept packets from users using the targeted WiFi network
- SMS and email attacks: SET will try to trick and generate a fake email to get credentials
- Web-based attacks: lets you clone a web page so you can drive real users by DNS spoofing or phishing attacks
- Creation of payloads (.exe): SET will create a malicious .exe file that, after executed, will compromise the system of the user who clicks on it
Highlighted features include:
- Fast penetration testing
- Integration with third-party modules
- Phishing attack generator
- Launch QRCode attacks
- Support for PowerShell attack vectors
There are several reasons changing the MAC address is important. I use MacChanger while pentesting a wireless network with MAC filtering enabled and have to assign an approved MAC address to the wireless adapter. Or just literally change to a random MAC while pentesting. To use MacChanger, follow this command pattern:
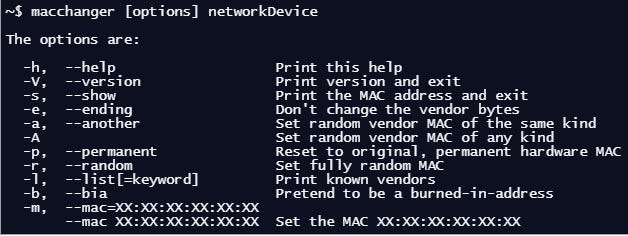
For example, I use my WLAN1 device to connect to the network, to change the default WLAN1 MAC address fully random, I type the command:

Traceroute is a computer network diagnostic tool for displaying the connection route and measuring transit delays of packets across an IP network.
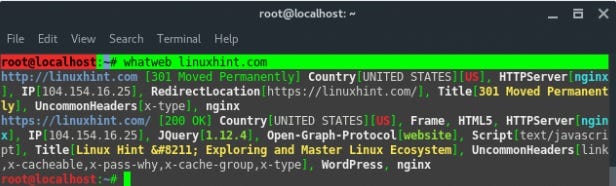
🔹WhatWeb🔹
WhatWeb is a website fingerprint utility. It identifies websites including content management systems (CMS), blogging platforms, statistic/analytic packages, JavaScript libraries, web servers, and embedded devices. WhatWeb has over 1,700 plugins, each to recognize something different. WhatWeb also identifies version numbers, email addresses, account IDs, web framework modules, SQL errors, and more.
🔹WHOIS🔹
WHOIS is a database managed by local internet registrars. It is a query and response protocol that is widely used for querying databases that store the registered users of an Internet resource, such as a domain name or an IP address block, but is also used for a wider range of other personal information about the domain owner.

🔹Nikto🔹
Nikto is a webserver and web application assessment tool to find potential security issues and vulnerabilities. Nikto scans for 6,700 potentially dangerous files/programs.
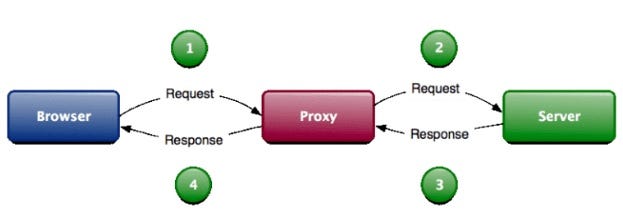
Burp Suite is a collection of tools bundled into a single suite which performs security testing of web applications, from initial mapping and analysis of an application’s attack surface, through to finding and exploiting security vulnerabilities. The main features of Burp Suite is that it can function as an intercepting proxy. Burp Suite intercepts the traffic between a web browser and the web server.
John the Ripper is one of the most popular password testing and cracking programs as it combines a number of password crackers into one package, auto-detects password hash types, and includes a customizable cracker. In Linux, ‘passwd’ file located at /etc/passwd contains all user information, hash SHA encrypted password of each of the users found is stored in /etc/shadow file.
JoomScan is a web application analysis tool to scan and analyze Joomla CMS, while WPScan is a WordPress CMS vulnerability scanner. To check what CMS is installed on a target website, you can either use ONLINE CMS Scanner, or using additional tools, such as “CMSMap.” Once you know the target CMS, whether it is Joomla or WordPress, then you can decide to use JoomScan or WPScan.
🔹Hash-Identifier and findmyhash🔹
Hash-Identifier is a tool to identify the different types of hashes used to encrypt data and especially passwords. Findmyhash is a tool to crack encrypted passwords or data using online services. For example, you have encrypted data such as : 098f6bcd4621d373cade4e832627b4f6. First thing you are going to need to do is identify the hash type. To do that, launch “hash-identifier” in a terminal, and input the hash value into it.
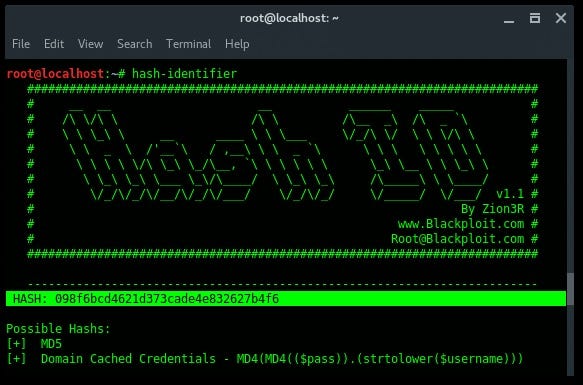
Hash-identifier detected this decrypted data and identified that it was using an MD5 hash algorithm. After its hash type is known, then we use another tool findmyhash to crack the data.
SQLiv is a simple and massive SQL injection vulnerability scanner.

Dirb is a tool to find hidden objects, files, and directories on a website. Dirb works by launching a dictionary-based attack against a web server and analyzes the response. Dirb comes with a set of preconfigured wordlists, located in /usr/share/dirb/wordlists/. to launch Dirb, use the following command pattern:

Have fun, and stay ethical, my friends.